
In this post I will display how you can use an Intune to silently enable Bitlocker on your devices. I will be using a Disk Encryption policy which can be found within the Endpoint security section of Intune.
I tested this on a Dell Latitude 5520 which has a TPM.
Within your Intune admin center, navigate to Endpoint security > Disk encryption & click Create Policy.

In the Create a profile pane, select the following:
Platform: Windows 10 and later
Profile: Bitlocker
Click Create.
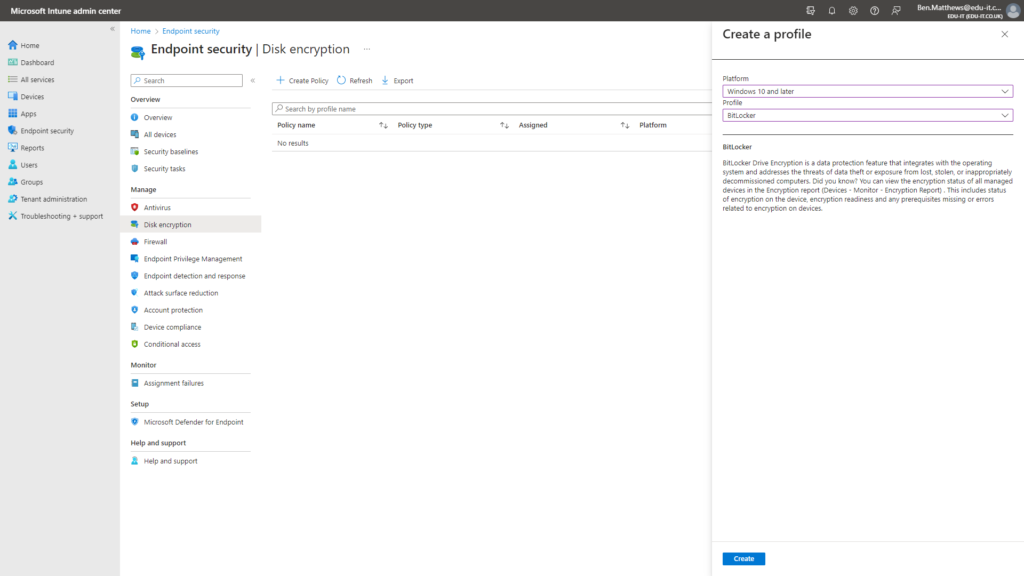
Enter a name for your new Profile.
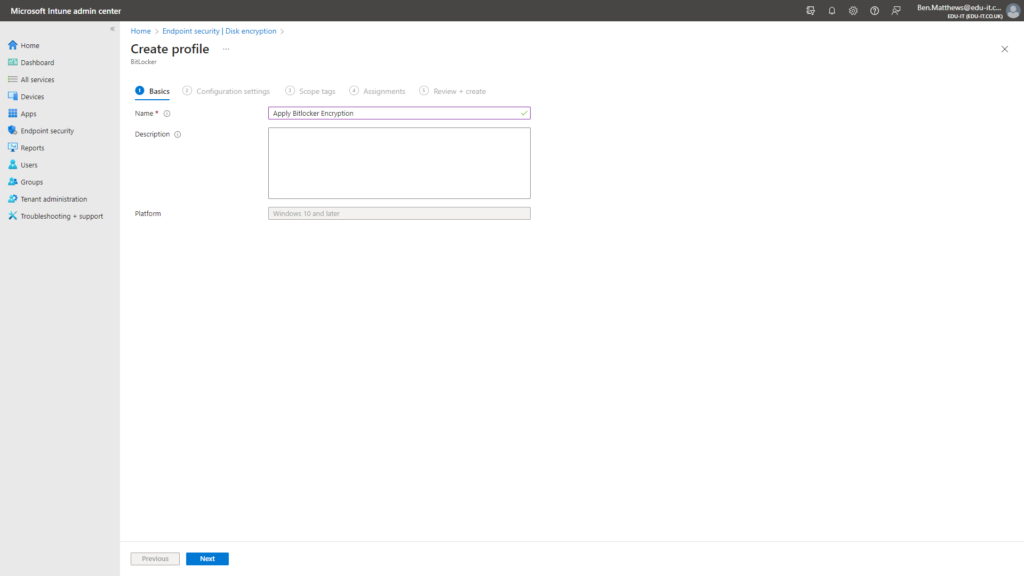
On the Configuration settings screen configure the following settings:
Bitlocker – Base Settings Further information here for each setting (MS Documentation)
- Enable full disk encryption for OS and fixed data drives: Yes
- Require storage cards to be encrypted (mobile only): Not configured
- Hide prompt about third-party encryption: Yes
- Allow standard users to enable encryption during Autopilot: Yes
- Configure client-driven recovery password rotation: Enable rotation on Azure AD and Hybrid-joined devices
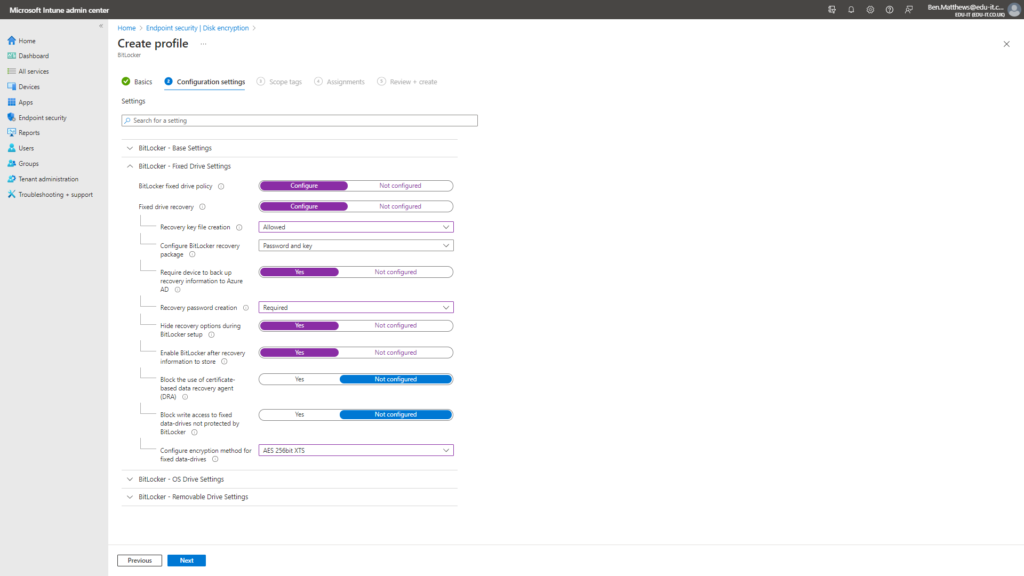
BitLocker – Fixed Drive Settings Further information here for each setting (MS Documentation)
- BitLocker fixed drive policy: Configure
- Fixed drive recovery: Configure
- Recovery key file creation: Allowed
- Configure BitLocker recovery package: Password and key
- Require device to back up recovery information to Azure AD: Yes
- Recovery password creation: Required
- Hide recovery options during BitLocker setup: Yes
- Enable BitLocker after recovery information to store: Yes
- Block the use of certificate-based data recovery agent (DRA): Not configured
- Block write access to fixed data-drives not protected by BitLocker: Not configured
- Configure encryption method for fixed data-drives: AES 256bit XTS
BitLocker – OS Drive Settings Further information here for each setting (MS Documentation)
- BitLocker system drive policy: Configure
- Startup authentication required: Yes
- Compatible TPM startup: Required
- Compatible TPM startup PIN: Blocked
- Compatible TPM startup key: Blocked
- Compatible TPM startup key and PIN: Blocked
- Disable BitLocker on devices where TPM is incompatible: Not configured
- Enable preboot recovery message and url: Not configured
- System drive recovery: Configure
- Recovery key file creation: Allowed
- Configure BitLocker recovery package: Password and key
- Require device to back up recovery information to Azure AD: Yes
- Recovery password creation: Allowed
- Hide recovery options during BitLocker setup: Yes
- Enable BitLocker after recovery information to store: Yes
- Block the use of certificate-based data recovery agent (DRA): Not configured
- Minimum PIN length: N/A
- Configure encryption method for Operating System drives: AES 256bit XTS
BitLocker – Removable Drive Settings Further information here for each setting (MS Documentation)
- BitLocker removable drive policy: Configure
- Configure encryption method for removable data-drives: AES 256bit XTS
- Block write access to removable data-drives not protected by BitLocker: Yes
- Block write access to devices configured in another organization: Yes


Click Next on the Scope tags screen.
I chose to assign this to a specific group that I had created.
Click Next.
Review your settings.
Your new Disk encryption policy will then be created.
I then navigated to Devices > All Devices, selected my test VM & clicked the Sync button to force it to check in.
Outcome
Once the policy applies to your devices the setting will take effect.
Profile Monitoring:
You can monitor the profile assignment status by selecting your newly configured Bitlocker policy.
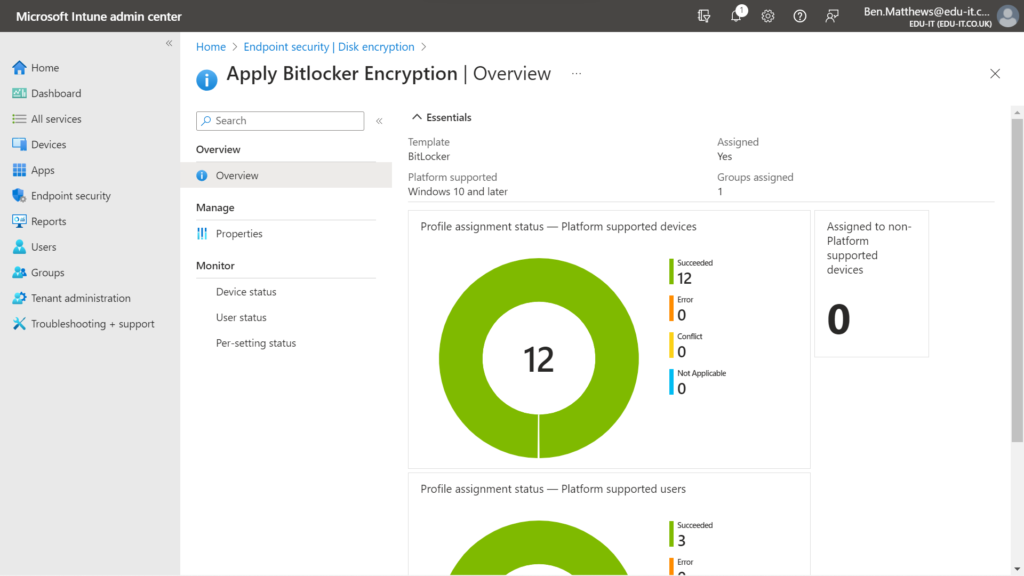
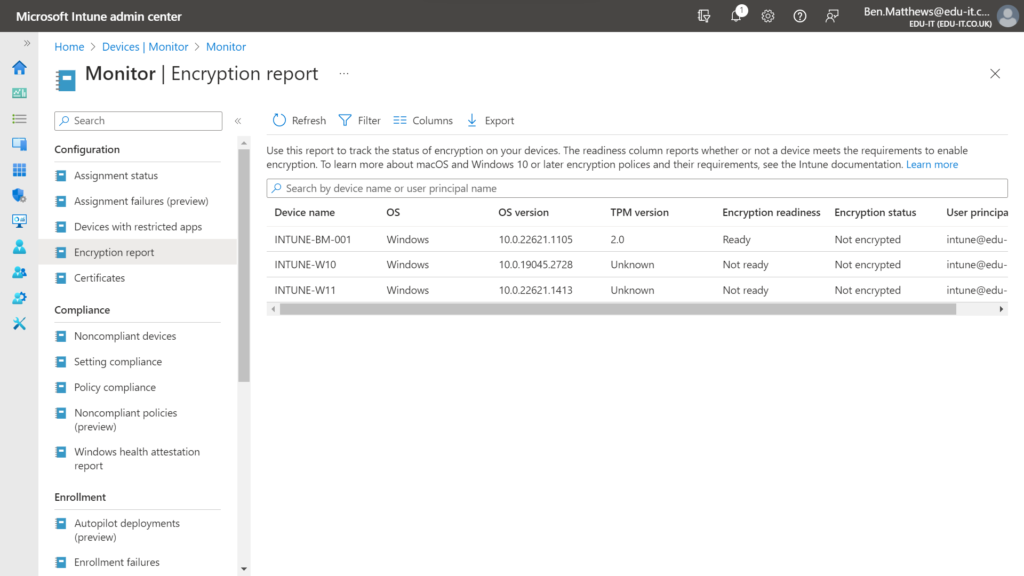
Encryption Report:
You can monitor the status of each device by viewing the Encryption report. This can be found via Devices > Monitor > Encryption report.
I personally found that it took quite a long time for the status to update.
Recovery keys:
Once the profile applies, the recovery keys for the drive should back up to Azure AD as per the settings in the policy. You can find these recovery keys by selecting your device in the Intune Admin Center & selecting the Recovery keys option on the left.
USB storage devices:
I plugged in a USB storage device that was not encrypted and I was prompted to Encrypt the device.
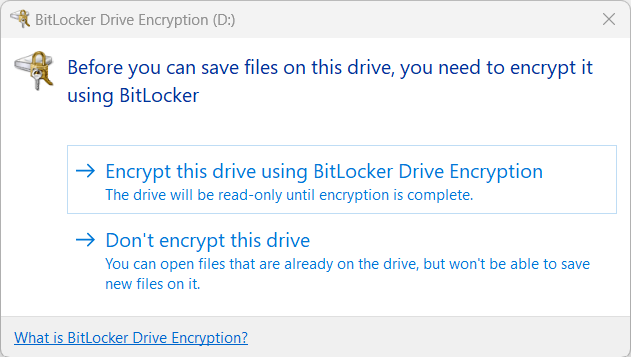
Overall I found that encrypting the OS drive took quite a long time for me, but the profiles & configuration did apply. I quite liked the USB storage device policy, prompting the user to immediately encrypt the device.
Thank you for reading.

